The Role Of Cryptography In Securing Bitcoin Transactions And The Blockchain

Cryptocurrency, particularly Bitcoin, has revolutionized the way we think about and use money. At the heart of this digital financial revolution lies a sophisticated system of encryption and cryptography that ensures the security and integrity of Bitcoin transactions. In this article, we will delve into the intricacies of how cryptography plays a pivotal role in safeguarding Bitcoin transactions and the blockchain.
Cryptography and the Basics of Bitcoin
Before we dive into the role of cryptography in securing Bitcoin transactions, it’s essential to understand some fundamental aspects of Bitcoin and the blockchain.

Cryptography in Bitcoin:
Cryptography is at the heart of Bitcoin’s security and functionality. It plays a pivotal role in ensuring the authenticity, security, and privacy of transactions. Here’s a detailed look at how cryptography is integrated into Bitcoin:
- Public and Private Keys:
- Public Key: In Bitcoin, users have a pair of cryptographic keys, a public key, and a private key. The public key is essentially an address to which others can send Bitcoin. It’s publicly known and can be shared freely.
- Private Key: The private key is kept secret and should only be known to the owner. It is used to create digital signatures, which are essential for authorizing transactions. The private key must be securely stored since anyone with access to it can control the Bitcoin associated with its corresponding public key.
- Digital Signatures:
- When a Bitcoin user initiates a transaction, they sign it with their private key. This creates a digital signature, unique to that transaction and the private key used.
- The digital signature serves as proof that the transaction is authorized by the rightful owner of the private key. It verifies the authenticity of the transaction and prevents unauthorized spending.
- Public Key Cryptography:
- Public key cryptography is the foundation of Bitcoin’s security. It enables users to verify the origin of Bitcoin and ensure that only the rightful owner can spend it.
- The recipient uses the sender’s public key to verify the digital signature. If the verification is successful, it means that the sender has control of the private key and, therefore, the authority to spend the Bitcoin.
- Hash Functions:
- Bitcoin relies on cryptographic hash functions to create a unique, fixed-length code for each transaction. This code is known as a transaction ID or hash.
- The hash is generated based on the data in the transaction, including the sender’s and recipient’s addresses, the amount, and a timestamp. The hash is like a digital fingerprint of the transaction.
- Altering even a single character in the transaction data would result in a completely different hash. This makes it practically impossible for anyone to tamper with the transaction’s data, as it would require changing all subsequent blocks in the blockchain.
Basics of Bitcoin:
Now that we’ve covered the cryptographic aspects, let’s delve into the fundamental concepts that underpin Bitcoin:
- Decentralization:
- Bitcoin operates in a decentralized manner. It doesn’t rely on a central authority, like a bank or government, to oversee transactions. Instead, a distributed ledger, known as the blockchain, records all transactions.
- This decentralization is a key feature that sets Bitcoin apart from traditional financial systems. It promotes transparency, security, and trust.
- Blockchain:
- The blockchain is a public ledger that contains a record of all Bitcoin transactions. It’s composed of blocks, with each block containing a set of transactions. Once a block is filled with transactions, it is added to the chain, creating an immutable history of all transactions.
- This transparency and immutability are crucial for the security and trustworthiness of the Bitcoin network.
- Mining and Proof of Work:
- The process of mining is integral to Bitcoin’s security and consensus mechanism. Miners compete to validate transactions and add them to the blockchain.
- Mining involves solving complex mathematical puzzles, a process known as proof of work. This ensures that it is computationally challenging to manipulate the blockchain, making it highly secure.
- Circulation and Supply:
- Bitcoin has a capped supply of 21 million coins. This scarcity is built into the protocol and contributes to its value proposition.
- Bitcoins are created as rewards for miners who validate transactions. Over time, these rewards decrease, mirroring a predictable issuance schedule.
Also, read – Top 10 Ways Web3 Help Fight Cybercrime In The Digital Era
Cryptography in Bitcoin Transactions
Cryptography is at the core of Bitcoin’s security model. Let’s explore how it plays a role in securing Bitcoin transactions:
Digital Signatures:
- Challenge: One of the fundamental problems in digital currency is preventing double-spending. Without a trusted intermediary, how can one ensure that a unit of currency isn’t spent more than once?
- Solution – Digital Signatures: Each Bitcoin transaction involves a digital signature created using a sender’s private key. A private key is a secret cryptographic key known only to the owner. This private key is used to sign a transaction, which serves as proof that the sender authorizes the transaction. The recipient can verify this signature using the sender’s public key. If the signature is valid, it means the sender has control of the private key and, therefore, the authority to spend the Bitcoin. This mechanism ensures the authenticity and integrity of the transaction.
“I struggled to understand it.”
Keep in mind… Hal was in the first #Bitcoin transaction, was involved in cryptography for over a decade, and predicted a $10 million #BTC two years before #Bitcoin ever first traded (for $0.06).
It takes time.
Patience.
🧡 https://t.co/Sclj7VSiQe— Luke Broyles (@luke_broyles) July 31, 2023
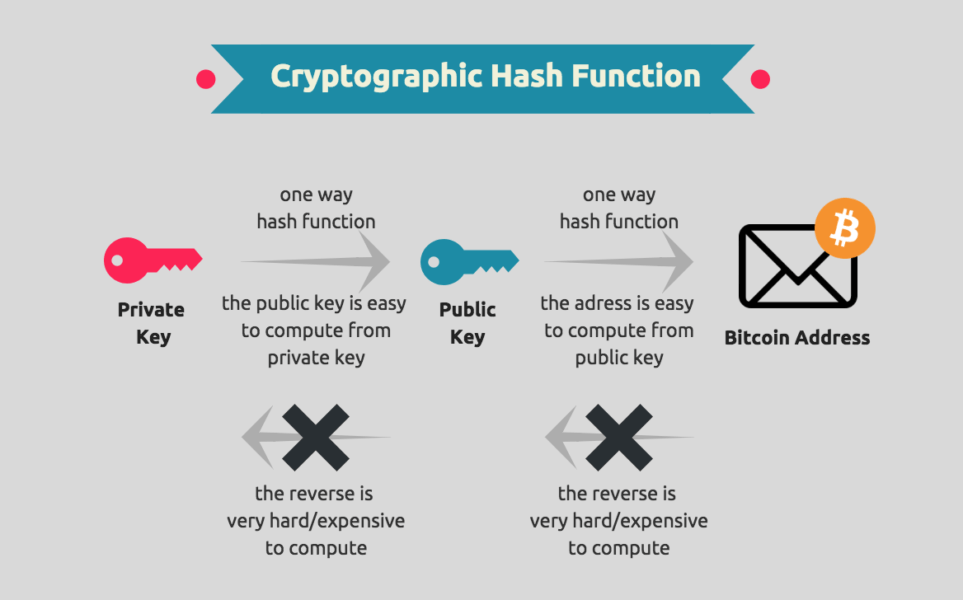
2. Public Key Cryptography:
- Challenge: How can the recipient be sure that the Bitcoin they receive is genuinely coming from the sender, and not an imposter?
- Solution – Public Key Cryptography: Bitcoin utilizes public key cryptography, which involves a pair of keys – a public key and a private key. The public key is like an address that can be shared with anyone, while the private key is kept secret. When a transaction is made, the sender uses their private key to create a digital signature. The recipient can then use the sender’s public key to verify the signature. This process ensures that only the legitimate owner of the private key can authorize transactions.
3. Hash Functions:
- Challenge: How can the Bitcoin network ensure the security and immutability of transactions and blocks in the blockchain?
- Solution – Hash Functions: Bitcoin relies on cryptographic hash functions to create a unique, fixed-length code for each transaction. This code is known as a transaction ID or hash. It’s generated based on the data in the transaction, including the sender’s and recipient’s addresses, the amount, and a timestamp. This hash serves as a digital fingerprint of the transaction. If even a tiny change is made in the transaction data, the resulting hash will be drastically different. This makes it extremely difficult for anyone to tamper with a transaction’s data, as it would require altering all subsequent blocks in the blockchain.
4. Mining and Proof of Work:
- Challenge: How can the Bitcoin network prevent fraudulent transactions and ensure the security and consensus of the blockchain?
- Solution – Mining and Proof of Work: Miners, who are participants in the Bitcoin network, compete to solve complex mathematical puzzles. This process is known as proof of work. Once a miner successfully solves a puzzle, they validate a set of transactions and add them to a new block on the blockchain. This process ensures the security and consensus of the network, making it highly resistant to fraudulent transactions. It also contributes to the decentralized nature of Bitcoin.
5. Address Generation:
- Challenge: How can users generate secure and private addresses for receiving Bitcoin?
- Solution – Address Generation: Cryptographic key pairs are used to generate Bitcoin addresses. The public key is hashed to create the recipient’s address, which is a string of letters and numbers. The private key, on the other hand, is used to control and authorize the spending of Bitcoin associated with that address. The address generation process is secure, making it difficult for others to determine the private key from the public key or address.
Challenges and Future Developments
While Bitcoin’s cryptographic security is robust, it is not entirely immune to potential threats. Quantum computing, for example, has the potential to break existing encryption algorithms. To address this, researchers are exploring post-quantum cryptography solutions.
- Post-Quantum Cryptography:
- Development: To mitigate the quantum computing threat, researchers and the cryptography community are actively working on post-quantum cryptography. Post-quantum cryptography refers to cryptographic algorithms that are resistant to attacks from both classical and quantum computers.
- Significance: Post-quantum cryptography is crucial for the long-term security of Bitcoin and other cryptocurrencies. It aims to replace the current cryptographic standards, such as ECDSA (Elliptic Curve Digital Signature Algorithm), with quantum-resistant alternatives.
- Quantum-Resistant Algorithms:
- Development: Researchers are exploring various quantum-resistant algorithms, such as hash-based cryptography, lattice-based cryptography, code-based cryptography, and multivariate polynomial cryptography. These algorithms are designed to withstand attacks from quantum computers.
- Adoption: Once quantum-resistant algorithms are thoroughly researched and tested, Bitcoin developers may consider integrating them into the blockchain’s protocol.
- Timely Transition:
- Consideration: Transitioning to post-quantum cryptography is not a simple task. It requires careful planning and coordination within the Bitcoin community. Existing keys and transactions may need to be migrated to quantum-resistant formats, and software and hardware support for the new algorithms must be developed.
- Quantum-Secure Wallets:
- Development: Wallet providers and developers need to create quantum-secure wallets that can generate and manage quantum-resistant key pairs. These wallets should be user-friendly and capable of seamlessly transitioning to new encryption standards.
- User Awareness: Educating Bitcoin users about the importance of migrating to quantum-secure wallets when the time comes is vital.
- Quantum Computing’s Timeline:
- Consideration: The timeline for practical quantum computing remains uncertain. It could be several years or even decades before quantum computers pose a real threat to Bitcoin’s security. Therefore, balancing the urgency of transition with the need for thorough research is essential.
- Ongoing Research and Collaboration:
- Development: The development of post-quantum cryptography is an ongoing process that requires collaboration between academia, industry, and the open-source community. Bitcoin developers and stakeholders should actively engage in this research and contribute to the development of quantum-resistant standards.
Conclusion
Cryptography is the linchpin of Bitcoin’s security. It ensures the authenticity of transactions, secures the blockchain, and makes the cryptocurrency resilient to fraud and tampering. Understanding the role of cryptography in Bitcoin is crucial for users, developers, and policymakers as they navigate the evolving landscape of digital finance. As technology continues to advance, cryptography will remain at the forefront of safeguarding the future of cryptocurrency.



























































