Top 10 Web3 Vulnerabilities: Know The Challenges and Solutions

Web3 refers to the third generation of the internet, which aims to transform the way we interact with digital content and services. While Web1 was characterized by static web pages and limited interactivity, and Web2 introduced dynamic web applications and social media platforms, Web3 is focused on decentralization, data ownership, and trustless interactions. It leverages blockchain technology and decentralized protocols to create a more open, transparent, and user-centric internet ecosystem.
The fundamentals of Web3 can be summarized as follows:
1. Decentralization: Web3 emphasizes decentralization, which means that power and control are distributed among participants rather than concentrated in a few central authorities. It leverages blockchain technology to create decentralized networks where data and applications are stored and processed across multiple nodes in a peer-to-peer manner. This eliminates the need for intermediaries, reduces the risk of single points of failure, and enhances security and censorship resistance.
2. Blockchain Technology: Web3 relies on blockchain technology as its foundational layer. Blockchains are distributed ledgers that record transactions or other data in a secure and transparent manner. They use cryptographic techniques to ensure data integrity and immutability. Web3 applications often utilize smart contracts, which are self-executing contracts with predefined rules and conditions encoded on the blockchain. Smart contracts enable trustless interactions between parties, eliminating the need for intermediaries.
3. Cryptographic Security: Web3 places a strong emphasis on security and privacy. It uses cryptographic techniques such as public-key cryptography to secure data and enable secure transactions. Users have control over their private keys, which are used to sign transactions and prove ownership of digital assets. This allows for secure and tamper-proof digital identity management and prevents unauthorized access to data.
4. Interoperability: Web3 aims to create a more interconnected internet ecosystem by promoting interoperability between different platforms and protocols. It enables seamless communication and data exchange between different blockchain networks and applications. This interoperability encourages collaboration, innovation, and the creation of decentralized ecosystems that span multiple domains.
5. User Empowerment: Web3 focuses on empowering users by giving them control over their data and digital assets. It promotes the concept of self-sovereign identity, where individuals have full ownership and control over their personal information. Users can selectively share their data with different applications and revoke access at any time. Additionally, Web3 enables the tokenization of assets, allowing users to directly own and trade digital assets without relying on intermediaries.
6. Open Governance: Web3 promotes open governance models where decision-making processes are transparent, inclusive, and decentralized. It enables stakeholders to participate in the decision-making process through mechanisms such as on-chain voting and community governance. This fosters a more democratic and community-driven approach to building and governing internet infrastructure and protocols.
7. Web3 Stack: The Web3 ecosystem comprises various layers that work together to enable decentralized applications (dApps) and services. These layers include the blockchain layer (e.g., Ethereum, Polkadot), the decentralized storage layer (e.g., IPFS, Filecoin), the identity layer (e.g., Decentralized Identifiers – DIDs), the decentralized finance layer (DeFi), and the decentralized application layer (dApps).
Web3 has the potential to revolutionize several industries and use cases. It can enable decentralized finance, where individuals have direct control over their financial assets and can access services such as lending, borrowing, and asset trading without relying on traditional intermediaries. It can transform supply chain management by providing end-to-end transparency and traceability. It can also revolutionize content creation and distribution, enabling creators to directly monetize their work and interact with their audience without relying on centralized platforms.
Overall, Web3 represents a paradigm shift in the way we think about the internet. By prioritizing decentralization, trust, and user empowerment, it aims to create a more open, inclusive, and equitable digital ecosystem that aligns with the original vision of the internet.
Also read: Is Web3 Going To Pave The Path Of Metaverse Digital World?
Why do you need to know the Web3 Vulnerabilities?
Understanding Web3 vulnerabilities is crucial for several reasons:
1. Security: Web3 applications operate in a decentralized and trustless environment, making them attractive targets for malicious actors. By being aware of potential vulnerabilities, developers and users can implement appropriate security measures to safeguard their assets and data. Understanding vulnerabilities helps in identifying weak points that can be exploited, such as smart contract bugs, cryptographic weaknesses, or vulnerabilities in the underlying blockchain protocol.
2. Risk Mitigation: Knowing Web3 vulnerabilities enables proactive risk mitigation. It allows developers and security auditors to conduct thorough assessments and audits of smart contracts, protocols, and decentralized applications. By identifying vulnerabilities early in the development process, appropriate fixes and mitigations can be implemented to minimize the risk of attacks, financial losses, and data breaches.
3. Protecting User Funds: Web3 applications often involve the management and transfer of digital assets, such as cryptocurrencies and non-fungible tokens (NFTs). Understanding vulnerabilities helps developers build robust systems that protect user funds from theft, fraud, or exploitation. This includes implementing secure wallet integrations, employing secure key management practices, and conducting comprehensive security audits.
4. Privacy and Data Protection: Web3 applications deal with sensitive user data, such as personal information, transaction history, and digital identities. Awareness of vulnerabilities helps in building privacy-preserving systems and protecting user data from unauthorized access or leaks. It involves employing strong encryption techniques, secure data storage practices, and implementing privacy-focused protocols.
5. Trustworthiness and Adoption: Web3 aims to create a trustless environment by reducing the reliance on intermediaries and centralized authorities. However, vulnerabilities can undermine this trust and hinder the adoption of Web3 technologies. By actively understanding and addressing vulnerabilities, the Web3 ecosystem can gain credibility and foster trust among users, investors, and the wider community.
6. Compliance and Regulatory Considerations: As Web3 evolves, governments and regulatory bodies are developing frameworks to govern its usage. Understanding vulnerabilities helps in designing Web3 systems that adhere to regulatory requirements and compliance standards. By addressing vulnerabilities, developers can demonstrate their commitment to security, privacy, and responsible innovation, which can facilitate regulatory compliance and wider acceptance.
7. Industry Reputation: Vulnerabilities and exploits in Web3 applications can have severe repercussions on the reputation of projects, platforms, and the entire Web3 ecosystem. News of hacks, exploits, or data breaches can undermine confidence in decentralized technologies and hinder adoption. By actively seeking knowledge about vulnerabilities and actively addressing them, the Web3 community can work towards maintaining a positive reputation and fostering user trust.
In summary, understanding Web3 vulnerabilities is essential to ensure the security, privacy, and trustworthiness of decentralized applications and protocols. It enables developers, auditors, and users to proactively identify and mitigate risks, protect user funds and data, comply with regulations, and maintain the reputation of the Web3 ecosystem.
Our interview series, Founding Web3, continues this week with Gregarius Narain, @gregarious, of @zealous_app
He tells us about his recent wins, challenges, and that one tool that would make his life a just little easier (spoiler alert: it's open-source apis!) … pic.twitter.com/VExpMbvjWq
— NEAR Horizon (@nearhorizon) June 21, 2023
What are Web3 Vulnerabilities?
Web3 vulnerabilities refer to the weaknesses or flaws present in decentralized applications (dApps), blockchain protocols, smart contracts, and other components of the Web3 ecosystem. These vulnerabilities can be exploited by malicious actors to gain unauthorized access, manipulate data, steal assets, or disrupt the normal functioning of Web3 applications. It is crucial to understand these vulnerabilities to effectively mitigate risks and enhance the security of Web3 systems. Here are some common Web3 vulnerabilities:
1. Smart Contract Bugs: Smart contracts are self-executing contracts with predefined rules encoded on the blockchain. However, errors or vulnerabilities in the contract’s code can lead to unexpected behaviors or exploitable loopholes. Common smart contract vulnerabilities include reentrancy attacks, integer overflow/underflow, improper access control, and unchecked external calls. These vulnerabilities can be exploited to drain funds, manipulate data, or disrupt the operation of the contract.
2. Blockchain Protocol Vulnerabilities: Blockchain protocols, such as Ethereum or Polkadot, can have vulnerabilities that impact the security and stability of the entire network. Protocol vulnerabilities may include consensus algorithm weaknesses, governance flaws, or vulnerabilities in the network’s underlying cryptographic algorithms. Exploiting these vulnerabilities can lead to network disruptions, double-spending attacks, or the compromise of the blockchain’s integrity.
3. Weak Cryptography: Cryptographic algorithms are fundamental to Web3 security. Weak encryption algorithms or improper implementation of cryptography can render sensitive data or transactions vulnerable to attacks. This can include weak key generation, insecure random number generation, or improper usage of cryptographic primitives. Cryptographic vulnerabilities can be exploited to access private keys, impersonate users, or decrypt encrypted data.
4. Decentralized Application Vulnerabilities: Decentralized applications built on Web3 technologies can have vulnerabilities similar to traditional web applications, including cross-site scripting (XSS), cross-site request forgery (CSRF), or SQL injection. These vulnerabilities can be exploited to gain unauthorized access, manipulate user data, or execute malicious code within the dApp’s interface.
5. Wallet Vulnerabilities: Web3 wallets, used to manage private keys and interact with decentralized applications, can be vulnerable to attacks. This includes phishing attacks, where users are tricked into revealing their private keys or interacting with malicious websites or applications. Wallet vulnerabilities can lead to the loss of user funds or unauthorized access to personal information.
6. Oracle Manipulation: Oracles are essential components that provide external data to smart contracts, enabling them to interact with real-world events. However, if the oracle is compromised or manipulated, it can provide incorrect or malicious data to the smart contract, leading to undesirable outcomes. Attackers can exploit vulnerabilities in oracles to manipulate prices, execute front-running attacks, or cause other disruptions to the contract’s functionality.
7. Interoperability Risks: Web3 aims to promote interoperability between different blockchain networks and applications. However, this introduces potential vulnerabilities when interacting with external systems. Inadequate validation or verification mechanisms during cross-chain transactions or data transfers can be exploited to perform attacks or manipulate data across different blockchain networks.
To address these vulnerabilities, various measures can be taken, including conducting comprehensive security audits, following best practices for secure smart contract development, performing regular penetration testing, implementing multi-factor authentication for wallets, using reputable oracles, and staying informed about the latest security practices and developments within the Web3 ecosystem.
Also read: Your Ultimate Guide To Web3 Bug Bounty: Variations, Vulnerabilities And Future
Top 10 Web3 Vulnerabilities
Web3 is the next generation of the internet, built on blockchain technology and decentralized networks. It promises to be more secure, private, and transparent than the current Web 2.0. However, Web3 is not without its security vulnerabilities.
Here are the top 10 Web3 vulnerabilities:
Smart contract logic hacks. Smart contracts are self-executing contracts that are stored on the blockchain. They are used to automate a wide range of transactions, such as financial agreements, voting, and property ownership. However, smart contracts can be hacked if there are flaws in their logic.

Reentrancy attacks. A reentrancy attack is a type of smart contract hack that occurs when a contract calls itself recursively. This can be exploited by an attacker to steal funds from the contract. 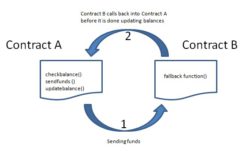
Code injection attacks. Code injection attacks occur when malicious code is injected into a smart contract. This can be done by exploiting a vulnerability in the contract’s code or by tricking the user into executing malicious code. 
Cryptojacking. Cryptojacking is a type of attack where a malicious actor steals a victim’s computing power to mine cryptocurrency. This can be done by exploiting a vulnerability in a website or by tricking the user into downloading a malicious file. 
Phishing attacks. Phishing attacks are a type of social engineering attack where the attacker sends a fraudulent message that appears to be from a legitimate source. This can be used to trick the victim into revealing sensitive information, such as their login credentials or cryptocurrency wallet address.

Rug pulls. A rug pull is a type of exit scam where the developers of a cryptocurrency project abandon the project and take the investors’ money. This is often done after the project has reached a certain level of popularity. 
Data manipulation in Dapps. Decentralized applications (Dapps) are applications that run on a blockchain network. They are often used to store sensitive data, such as financial information or personal identification data. However, Dapps can be vulnerable to data manipulation attacks, where an attacker can change the data stored on the blockchain.
Insecure credential storage. Credentials, such as passwords and API keys, are often stored in smart contracts. However, if these credentials are not stored securely, they can be stolen by an attacker.
Vulnerability in libraries. Smart contracts often rely on third-party libraries. If these libraries contain vulnerabilities, they can be exploited by an attacker to hack the smart contract. 
Human error. Human error is a major factor in many security vulnerabilities. This includes mistakes made by developers, users, and auditors.
![]()
These are just some of the top Web3 vulnerabilities. It is important to be aware of these risks and to take steps to protect yourself. Some of the things you can do to protect yourself include:
- Only interact with trusted Dapps.
- Do your research before investing in a cryptocurrency project.
- Use strong passwords and two-factor authentication.
- Keep your software up to date.
- Be aware of the latest security threats.
By following these tips, you can help to protect yourself from the top Web3 vulnerabilities.
Future of Web3
The future of Web3 holds immense potential for transforming various aspects of our lives and reshaping the internet as we know it. Here are some key areas that highlight the potential future developments of Web3:
1. Decentralized Finance (DeFi): DeFi has been one of the most prominent use cases within the Web3 ecosystem. In the future, DeFi is expected to expand further, offering a broader range of financial services such as lending, borrowing, insurance, derivatives, and asset management. DeFi protocols are likely to become more user-friendly, secure, and scalable, attracting a larger user base and facilitating mainstream adoption.
2. Web3 Applications and Services: As Web3 technologies mature, we can expect the development of a wide range of decentralized applications and services across various industries. This includes decentralized social media platforms, decentralized marketplaces, decentralized identity management systems, decentralized content creation and distribution platforms, and more. These applications will prioritize user privacy, data ownership, and user-centric experiences, providing alternatives to the centralized platforms dominant today.
3. Internet of Things (IoT) Integration: Web3 has the potential to enhance the interoperability and security of IoT devices by leveraging blockchain and decentralized protocols. IoT devices can interact directly with each other, exchange data securely, and execute transactions autonomously through smart contracts. This enables secure and transparent management of IoT networks, facilitates machine-to-machine payments, and ensures data integrity and authenticity.
4. Enhanced Privacy and Data Ownership: Web3 aims to empower users by giving them greater control over their data and digital identities. In the future, we can expect advancements in privacy-focused technologies, such as zero-knowledge proofs, secure multiparty computation, and decentralized identity solutions. These innovations will allow users to selectively share their data, protect their privacy, and have ownership and control over their personal information.
5. Interoperability and Cross-Chain Collaboration: Web3 is expected to foster greater interoperability between different blockchain networks, enabling seamless communication, data transfer, and transaction interoperability. Cross-chain bridges and interoperability protocols will facilitate collaboration between different blockchain ecosystems, opening up opportunities for decentralized applications to leverage the strengths of multiple networks.
6. Governance and DAOs: Web3 promotes decentralized governance models, where decision-making processes are transparent, inclusive, and community-driven. Decentralized Autonomous Organizations (DAOs) will play a significant role in the future of Web3, enabling stakeholders to participate in decision-making, fund projects, and shape the direction of protocols and platforms. DAOs will provide a framework for decentralized governance, allowing individuals to collectively manage resources and make decisions without relying on centralized authorities.
7. Web3 Scaling Solutions: As the usage of Web3 applications increases, scalability becomes crucial. Layer 2 scaling solutions, such as state channels, sidechains, and rollups, will enable Web3 applications to handle large-scale transactions efficiently, reducing congestion and costs on the underlying blockchain networks. These scaling solutions will improve the user experience, lower transaction fees, and enhance the overall scalability of Web3 applications.
8. Regulatory Frameworks and Compliance: As Web3 technologies continue to evolve, regulatory frameworks are likely to emerge to address legal and compliance aspects. Governments and regulatory bodies will work on establishing guidelines for decentralized finance, taxation, identity management, and consumer protection. Balancing regulatory requirements with the ethos of decentralization will be an ongoing challenge.
In summary, the future of Web3 holds exciting prospects for a more decentralized, secure, and user-centric internet ecosystem. It will transform various industries, empower individuals, redefine financial systems, enhance privacy and data ownership, and facilitate collaboration on a global scale. Continued innovation, collaboration, and adoption of Web3 technologies will shape the path towards this future vision.



























































